Deep dive into SEANCE Threat Modelling Framework
SEANCE is a threat modelling framework tailored for micro businesses (i.e., businesses with fewer than 10 employees and a turnover of no more than €2 million). It is a non-technical, asset-centric framework that aims to be easily understood and used by micro business (MB) owners who do not have the cybersecurity expertise or resources (i.e. financial and otherwise) to use an existing framework, tool, or system to identify the threats to their business.
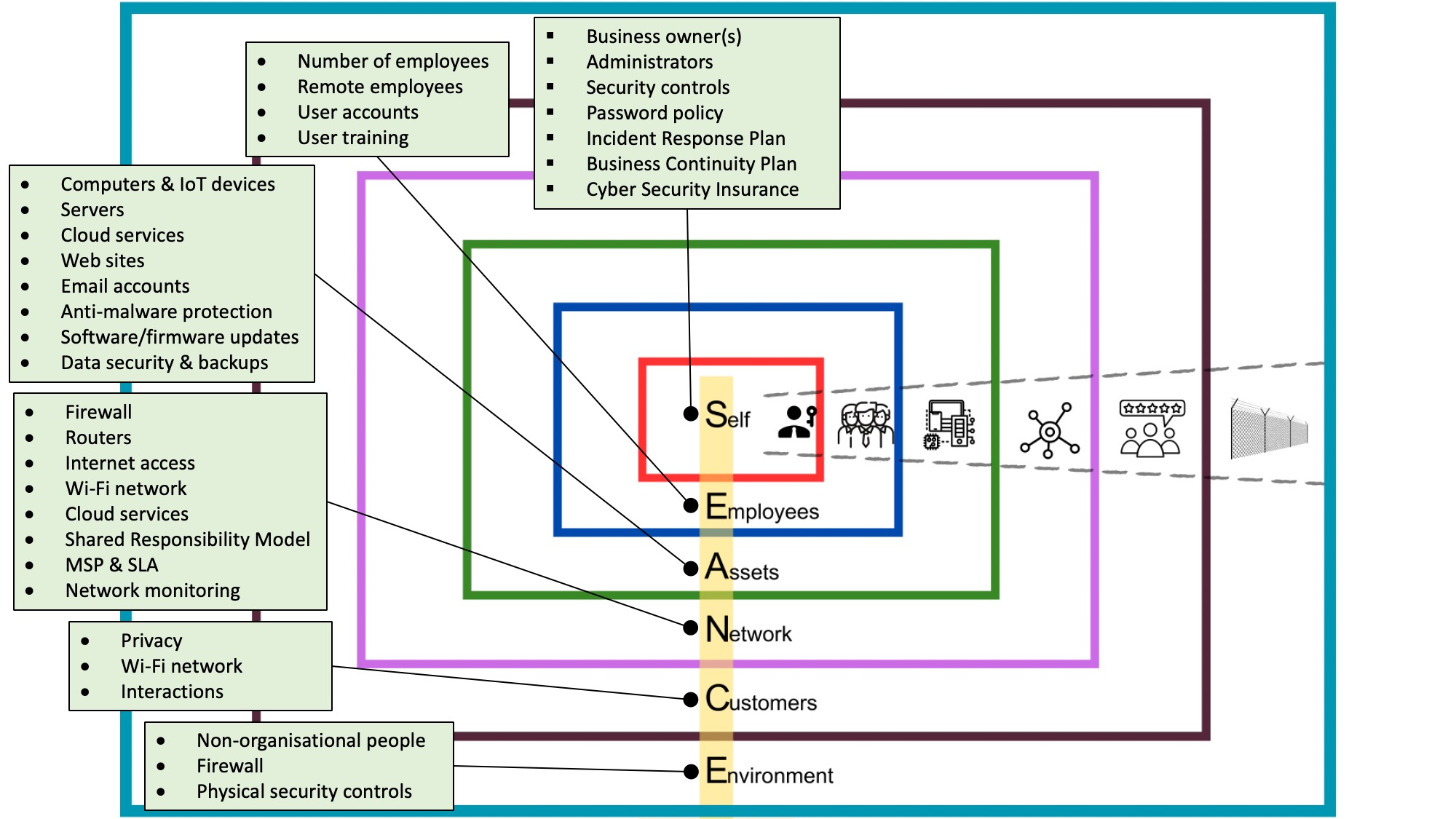
The SEANCE framework provides for threats to be considered and assessed in six layers, with the general assumption that the most dangerous threat is the closest threat. The underlying logic is that a weakness in an inner layer will propagate to other layers; therefore, weaknesses in the inner layers are prioritised over the outer layers. For example, if the owner of the micro business (layer 1) does not enforce a password policy, the employees (layer 2) are much less likely to use strong passwords. Therefore, when considering threats to your business, you should think about your:
- Self
- Employees
- Assets
- Network
- Customers
- Environment
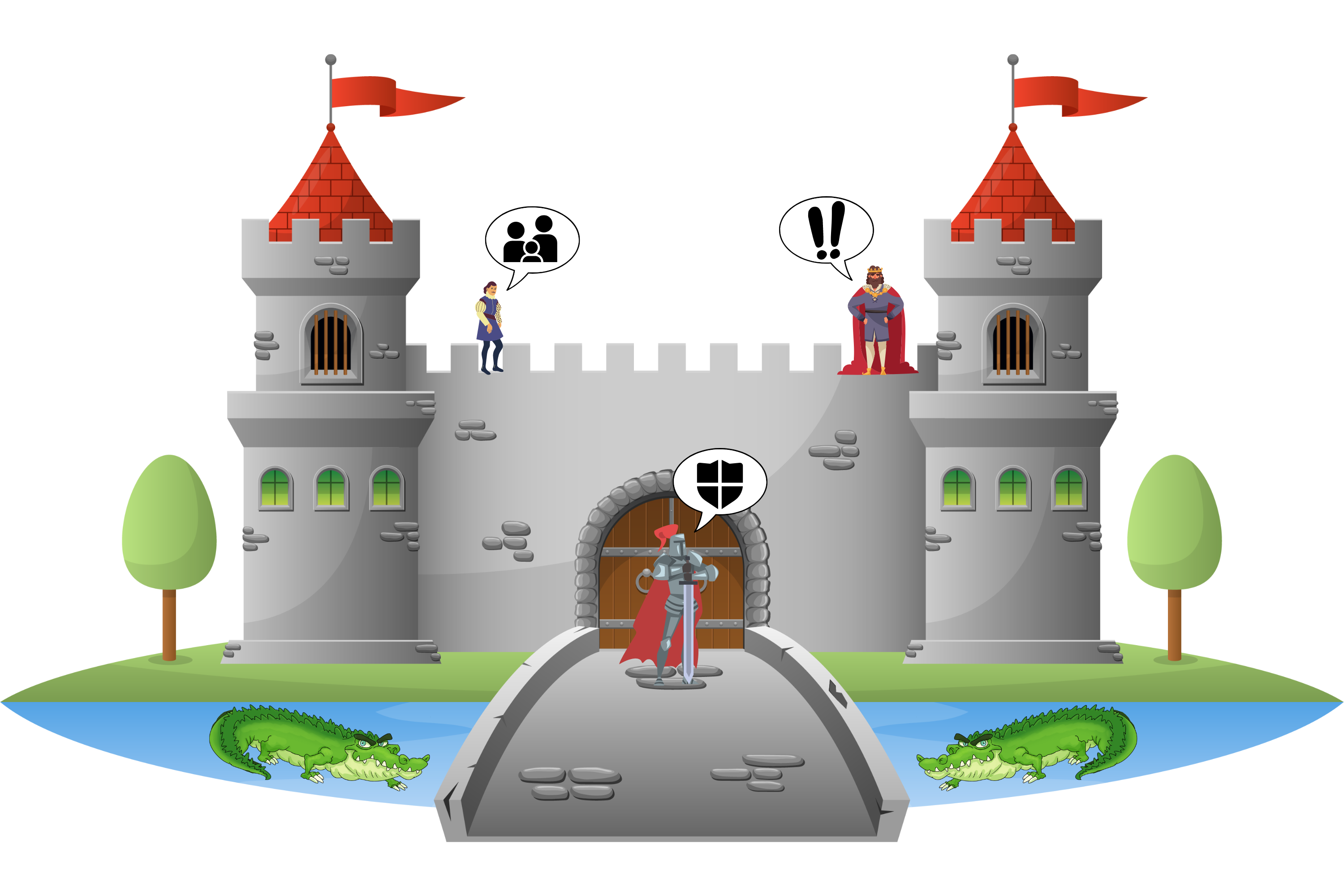
You can think of your organisation as a medieval castle: The lord (or commander for that matter) of the castle makes all the important decisions himself that have an impact on the whole castle. His army of warriors (in local jargon, his employees) carry out his decisions by using their weapons and other assets in accordance with his wishes. This is not an individual endeavour, however; it requires a castle-wide network to coordinate the deployment of weapons and smaller units, with the ultimate goal of keeping the castle's defensive posture in sync. Then there are the people who live within the castle's perimeter, who are usually unaware of their lord's important defensive decisions, and who are more concerned with the livelihood of their household, paying their lord to be exempted from military service - perhaps that's why the lord mocks them by referring to them as his customers at his festive dinners (where he may consume too much beer). The castle's environment then has a huge impact on the castle's security: Unlike a peaceful castle on a remote island, about which the local population hears (and dreams) a lot, the castle is surrounded by the castles of malevolent neighbouring kingdoms. The lord tries to fortify the castle by digging deep moats around it, filling them with water and putting hungry alligators in them. But there is one thing to remember: No matter what he does to fortify the perimeter, the castle is only as strong as the resilience of the lord and the integrity of his army! Therefore, the ruler prioritises threats from the inside of his castle over those from the outside.
Please note that SEANCE Micro Business Threat Modelling Framework is not intended to be a complete cyber security solution for micro businesses, but rather to improve their cyber security posture by raising awareness of cyber threats and providing a starting point for implementing industry standard security controls.
Let's now dive into the six layers of the SEANCE framework, starting from the innermost layer and working our way outwards. You may notice that some themes, such as "Setting up firewalls", appear in more than one layer, because they are relevant to different layers.
This is the innermost layer, where you consider the threats to yourself as well as the security controls you set up and manage. If your business is not wholly owned or controlled by you and you have other partners, they should also be considered in this layer.
| Key Themes | Guiding Questions |
|---|---|
| Business owner(s) Administrators Organisation-wide security controls Password policy Incident Response Plan Business Continuity Plan Cyber Security Insurance |
Are you the sole owner of the business or are there other shareholders/partners who run the business with you? -> How many shareholders/partners do you have? Do you carry out the administrative tasks yourself, or do you have a designated admin? -> Do you share your admin password with anyone else? Do you have and enforce a password policy? -> Does your password policy recommend that users create a different and unique password for each system they access? -> Does it provide guidance to users on how to create strong passwords? -> Does it specify the technical controls for measuring and managing the quality of passwords? -> Is there a process in place to detect and change the compromised passwords? -> Are there any safeguards in place to prevent passwords from being guessed by randomly trying all possible combinations (also known as “Brute Force”)? Do you have a policy for creating and deleting user accounts? -> Is there a policy for creating a new user account? -> Are there any procedures in place to monitor user accounts as employees join and leave the organisation? Do you have a policy for managing administrator accounts? -> Are you the only user with administrator privileges in the administration? -> If you are the only administrator in the organisation, do you share your admin account credentials with anyone else? -> Do you have a specific procedure that you follow and/or do you require an employee to go through a specific process before granting administrative privileges to an employee? -> Are there procedures to keep administrator users from using administrator accounts for everyday tasks/activities? -> Are administrator passwords protected by multi-factor authentication (MFA)? Do you have an incident response plan in place in the event of a cyber security incident? -> Are you aware of any possible legal reporting requirements and/or information sharing with the legal authorities? Do you have a business continuity plan to get your business back up and running as quickly as possible? Do you have a cyber security insurance in place to cover or reduce the financial risks caused by cyber security events? |
This layer consists of considerations related to all of your organisation's employees. This can include full-time and part-time employees, as well as volunteers, temporary or seasonal workers, etc.
| Key Themes | Guiding Questions |
|---|---|
| Number of employees Remote employees User accounts User training |
How many employees do you have? Do you have any remote employees who need to access to company assets remotely? -> How many remote employees do you have? -> Do any remote employees have administrator privileges? -> Do remote employees change their computer/smartphone settings to stop automatic connections to public Wi-Fi? -> Do remote employees enable full disk encryption on the devices that they use to connect to your network? -> Do you require the employees to use secure connections when connecting remotely to your network? These measures may include: (1) Using a router with WPA2 or WPA3 encryption when connecting from home. (2) Using a VPN when connecting via public Wi-Fi. Do you regularly brief and train all employees on the procedures and processes related to the organisation's cyber security measures and policies? -> Do our employees know how to recognise and report common attacks (e.g. phishing, ransomware, etc.)? -> Do your employees know how to perform basic cyber hygiene tasks? Do you have a password policy for the users? -> Does it encourage/enforce users to choose unique and strong passwords for their accounts? -> Does it enforce that everyone uses their own account and that there are no shared accounts? |
This layer includes all the assets your organisation owns. An asset can be broadly described as something of value to your business that you want to protect. Assets include computers, servers, data stores, websites, thin clients, self-service terminals, tablets, smartphones and any other device or digital tool that is essential to the business or that are used by you and your employees.
| Key Themes | Guiding Questions |
|---|---|
| Computers (desktops, laptops, thin clients, terminals, etc.) Servers Cloud services Web sites Email accounts IoT devices Anti-virus/malware protection Software/firmware updates Data security Data backups Point of Sale (POS) System |
How many computers do you use to run your business? Consider all the desktop and laptop computers that you use to store data, manage orders, and communicate with the customers. Do you keep an inventory of your assets? -> Do you keep track of the designated users and administrators of each device? -> Do you record the type of data that is stored on each device? -> Do you assess the risk of losing access to each device? Do you operate your own servers? -> Do you administer the servers yourself or do you delegate this to one of your employees? -> Do you have procedures for who can access and configure servers and how? Do you use a cloud service provider to store data, run a business application, etc.? -> Have you enabled MFA for the administrator and user accounts to access and/or manage the cloud services securely? -> Do you administer the cloud services yourself or do you delegate it to one of your employees? -> Is the administrator account shared between you and your employees, or is it kept confidential for one user? -> Is the administrator account used for day-to-day activities? -> Are you aware of the Shared Responsibility Model? Do you use Software as a Service (SaaS) products such as Google Docs, Microsoft365, etc.? Do you use IoT devices? -> Have you changed the default passwords? Have you set strong passwords? -> Do you keep the software/firmware up to date? Have you enabled automatic updates for all of your applications, including the operating system (OS)? -> If not, do you have a process in place to apply all critical updates in a reasonable amount of time? Are you using software that is no longer supported? -> If so, do you disconnect the devices that are running unsupported software from the Internet? Do you review your devices regularly and disable or remove unused software? Are you making sure that all accounts on your devices and cloud services are only those that are used as part of your day-to-day business? Have you disabled Auto-Run and Auto-Play on all your devices? Do you lock your mobile devices with a locking mechanism like a password, fingerprint, facial recognition, etc.? Do you ensure that all default passwords on all devices are changed? Have you taken necessary measues to protect your devices (including computers, laptops, tablets and mobile devices) against malware by installing anti-malware software or only allowing a certain set of apps to be installed? Do you restrict the installation of third-party (unsigned) applications outside the official application stores? Do you keep your sensitive and critical data encrypted when it is stored (at rest) or while it is being transmitted (in transit)? -> Do you enable full disk encryption (FDE) on your devices? -> If FDE is not enabled or available, do you encrypt sensitive files, folders, or databases individually? -> Do you use Virtual Private Network (VPN) solutions to encrypt the network traffic? Do you securely delete and/or destroy the data that is no longer in use? Do you have a procedure in place for regularly backing up your data? If so: -> How often do you back up your data? -> If you need to restore data from the last backup, how long does it take? Do you have a website? If so: -> Do you have an SSL certificate? -> Are you using HTTPS instead of HTTP? -> Do you have a Web Application Firewall (WAF) in place? -> Do you allow users to create accounts on your website? If so: - Do you enforce Multi-Factor Authentication (MFA) for the users? -> Do you accept online orders on your website? -> Do you accept online payments? If so: - Is your payment service provider PCI DSS compliant? Do you have procedures in place to safely dispose of and destroy devices (i.e. hard drives, flash drives, etc.) that are no longer in use? Do you use a Point of Sale (POS) system? If so: -> Is your system PCI DSS compliant? -> Do you keep the POS devices physically secure? -> Do you keep POS software and firmware up to date? -> Do you monitor POS device activity for potential suspicious activity? -> Have you changed the default passwords on your POS devices, and do you keep your passwords secure? -> Do you keep POS devices secure after hours? -> Do you have a clear policy on who can use POS devices? -> Is your POS system connected to a network to which customers and visitors can connect? |
Network is the digital heartbeat of your micro business, seamlessly connecting all your devices - like computers, tablets, and smartphones - so they can talk to each other and the wider world. Think of it like a team of friends who can easily talk, share photos, or even work on projects together, regardless of where they are. This setup helps your business run more efficiently, enabling tasks like sending emails, sharing files, and accessing the internet seamlessly.
| Key Themes | Guiding Questions |
|---|---|
| Firewall Routers Internet access Wi-Fi network Cloud services Shared Responsibility Model Managed Service Provider (MSP) Service Level Agreement (SLA) Network monitoring |
Is your business network protected by a firewall (or a router with firewall capability)? If so: -> Have you changed all passwords from the default passwords on your firewalls and internet gateways and are all passwords difficult to guess? -> If you thought that passwords had been exposed (i.e. someone who knew your password had left the organisation), would you be aware of this and change the password? Do you have any services enabled that can be accessed externally? Can your routers or hardware firewalls be configured remotely over the Internet? If so: -> Have you secured the administrator account and passwords and not shared them across the organisation? Have you configured your routers or your hardware firewalls to block all other services being advertised to the Internet? Do you keep the firmware on your router(s) updated? Do you use the services of a third-party Managed Service Provider (MSP) to manage your network and network devices and to monitor the devices and networks for suspicious activity? If so: -> Is there an appropriate SLA between you and the MSP? Do you use cloud services in your organisation? If so: -> Do you have a list of the cloud services you use? -> Have you enabled MFA for the administrator and user accounts to access and/or manage the cloud services you use? -> Have you located and understood the shared responsibility model for the cloud services you use? Do you allow people outside your organisation (e.g. customers, suppliers, etc.) to connect to the same Wi-Fi network that your business assets are connected to? If so: -> Have you ensured that the business assets are behind a firewall? |
While customers are vital to the financial longevity of your business, they also need to be treated with the utmost care when it comes to your organisation's cyber security. As they are the most important group of people outside the organisation, you should carefully manage the relationship between customers and business assets. On the other hand, although they are external to the organisation, customers need to penetrate the external boundaries of the organisation in a structured way in order to receive services from you.
| Key Themes | Guiding Questions |
|---|---|
| Privacy Wi-Fi network |
Do you collect personally identifiable information (PII) from customers for any purpose (marketing, research, etc.)? Do you allow users to create and maintain accounts on your site? If so: -> Do you comply with the privacy regulations depending on your jurisdiction (e.g. GDPR, DPA, etc.)? -> Do you enforce Multi-Factor Authentication (MFA) for the users? -> In the unlikely event of a customer data breach, do you have a process in place to notify and update affected customers? Do you allow customers to connect to the same Wi-Fi network that your business assets are connected to? If so: -> Have you ensured that the business assets are behind a firewall? How do customers interact with your assets, network, employees, and yourself? |
The outermost layer refers to the external boundaries of your organisation. So far, all considerations have been about the assets and people that are part of the organisation, including customers as explained in the previous layer. This layer considers all threats and threat actors outside the organisation's perimeter.
| Key Themes | Guiding Questions |
|---|---|
| Non-organisational people Firewall Physical security controls Fire safety Power outage Theft |
Do you have a firewall enabled to filter/block incoming external traffic? Approximately how many people from outside your organisation, other than customers, visit your workplace (per day/week/month/year)? Think of suppliers, government officials, etc. -> Do you keep a record of the non-organisational visitors? -> Have you noticed a sudden increase in the number of non-organisational visitors? -> Do you allow them to connect to your Wi-Fi network? Do you have physical security controls (e.g. cameras, locks, etc.) in place to secure the external perimeter of the organisation? Do you have the necessary fire safety measures in place, including smoke detectors and fire extinguishers? Do you have uninterruptible power supplies (UPS) in place to keep critical equipment running and prevent data loss in the event of a power outage? |